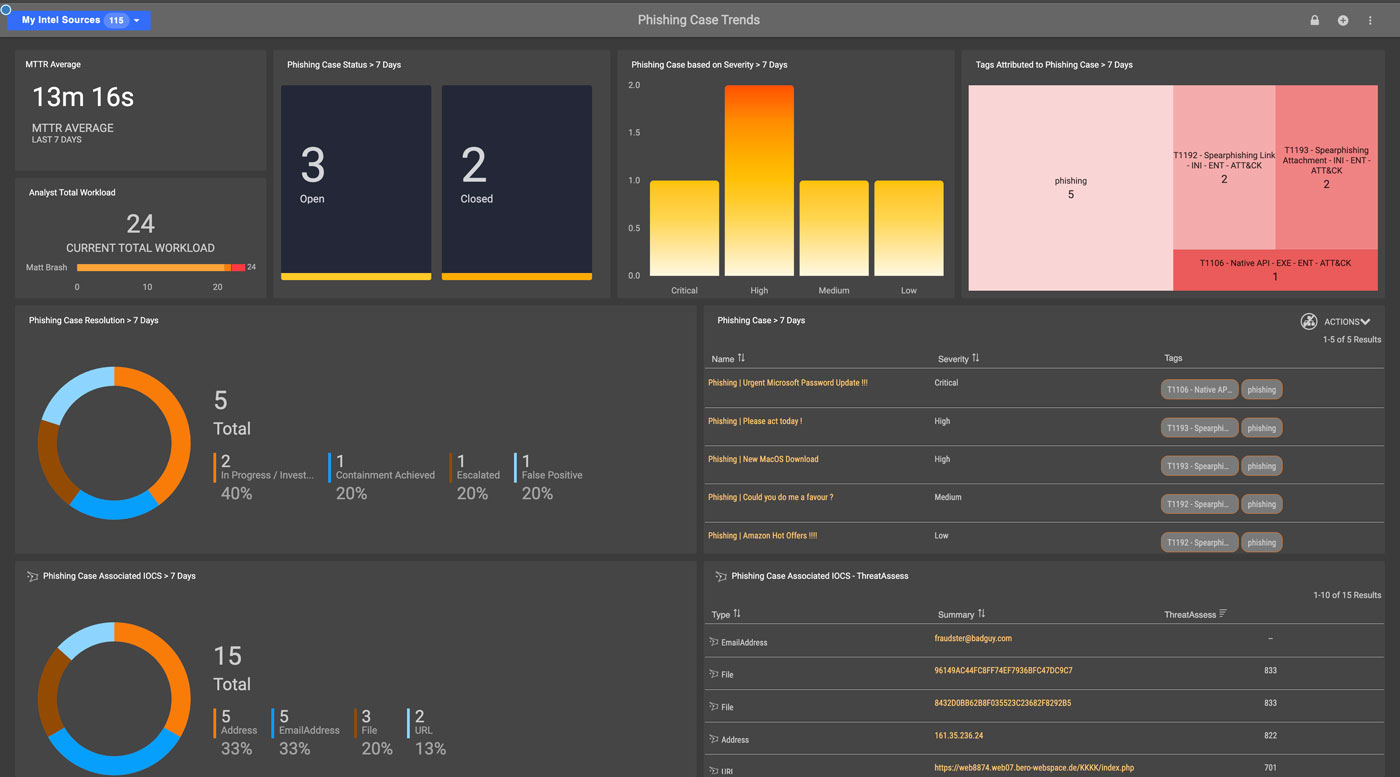
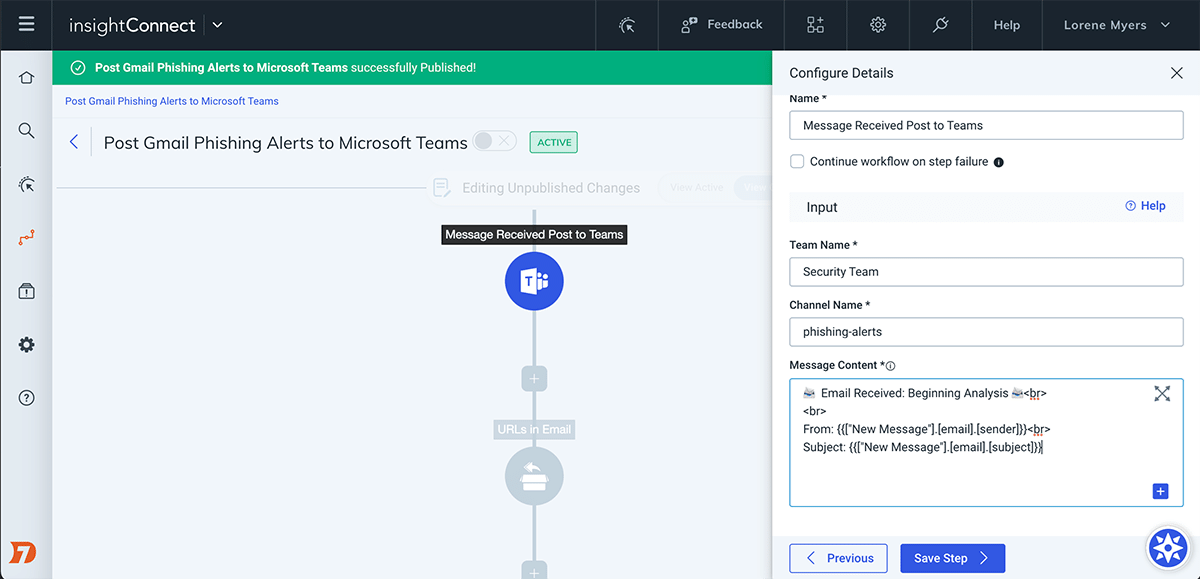
Eliminate Manual Threat Analysis of Credential Phishing and Malware Threats With Splunk Attack Analyzer | Splunk
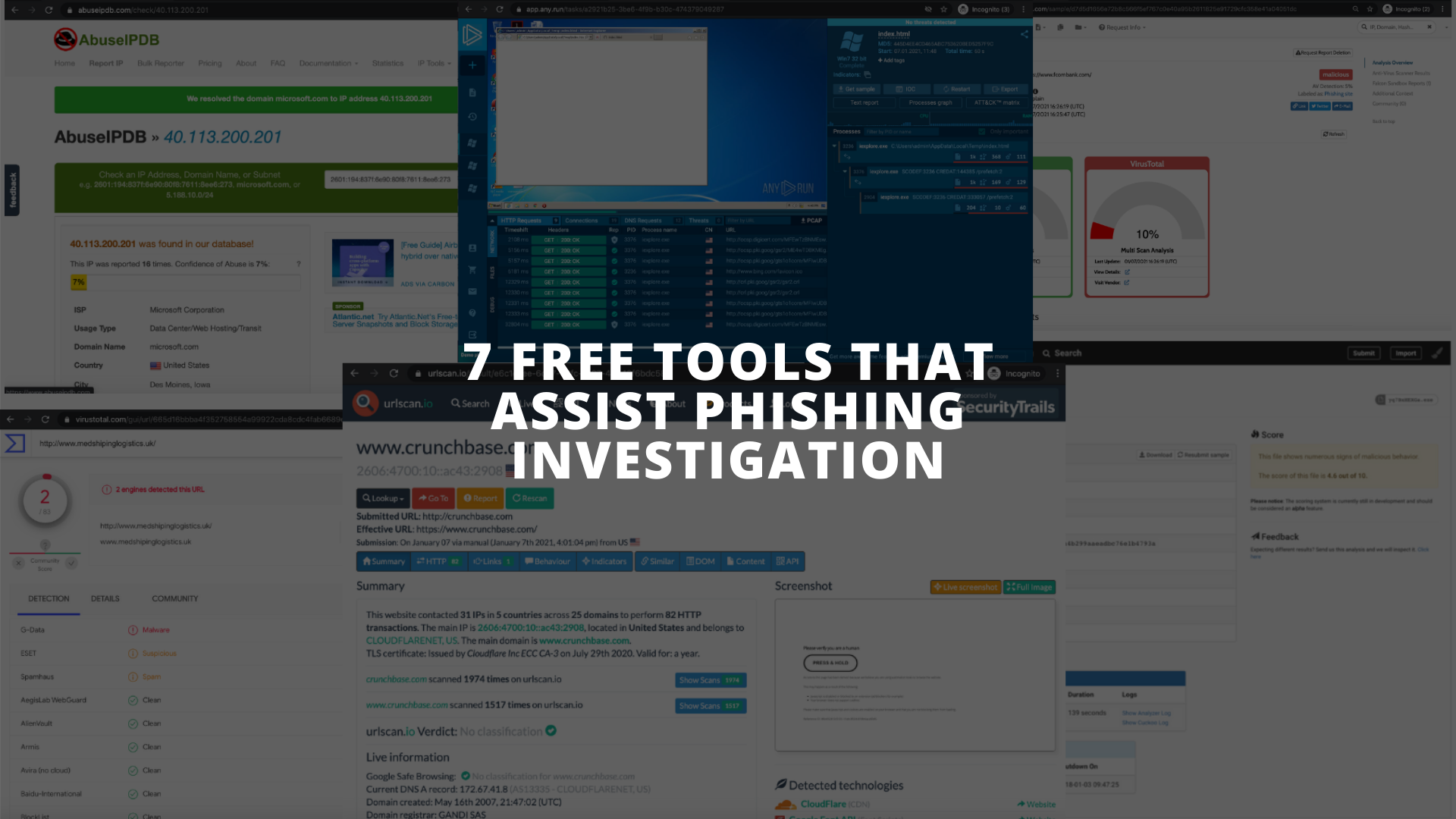
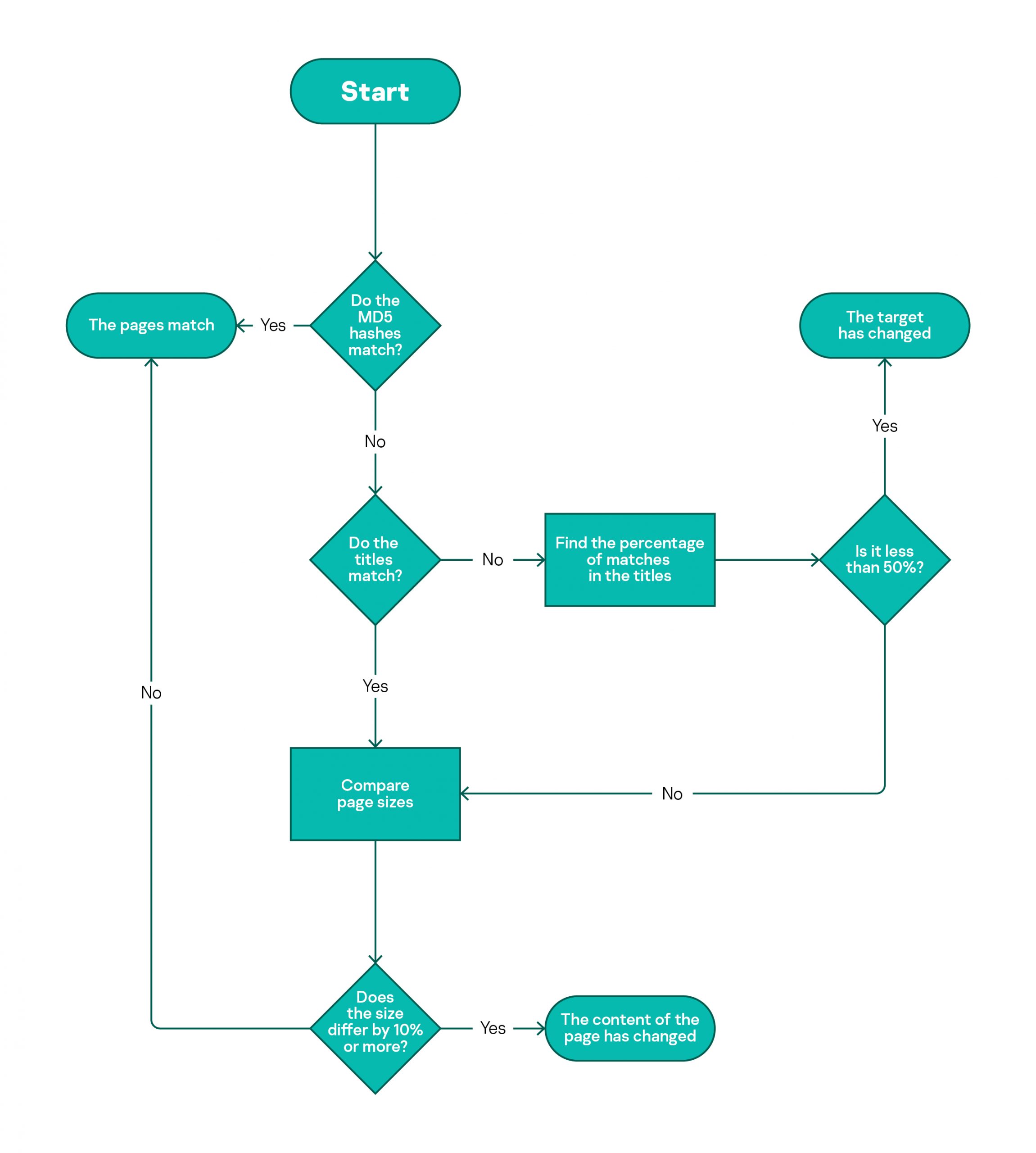
![PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/331bb7717f236ef1439ae66432b7b47f668918c5/6-Figure1-1.png)
PDF] Performance Analysis of Anti-Phishing Tools and Study of Classification Data Mining Algorithms for a Novel Anti-Phishing System | Semantic Scholar

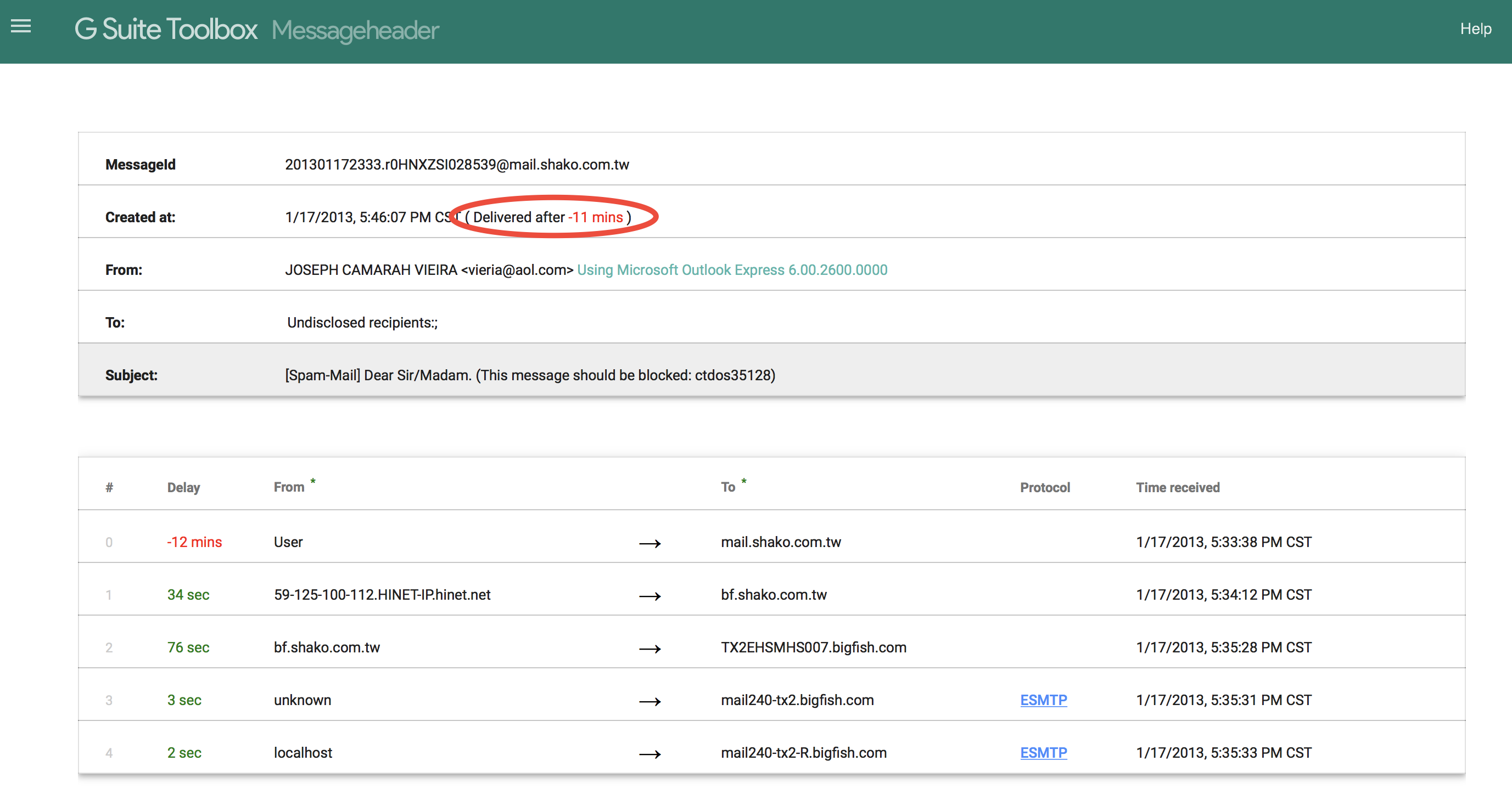
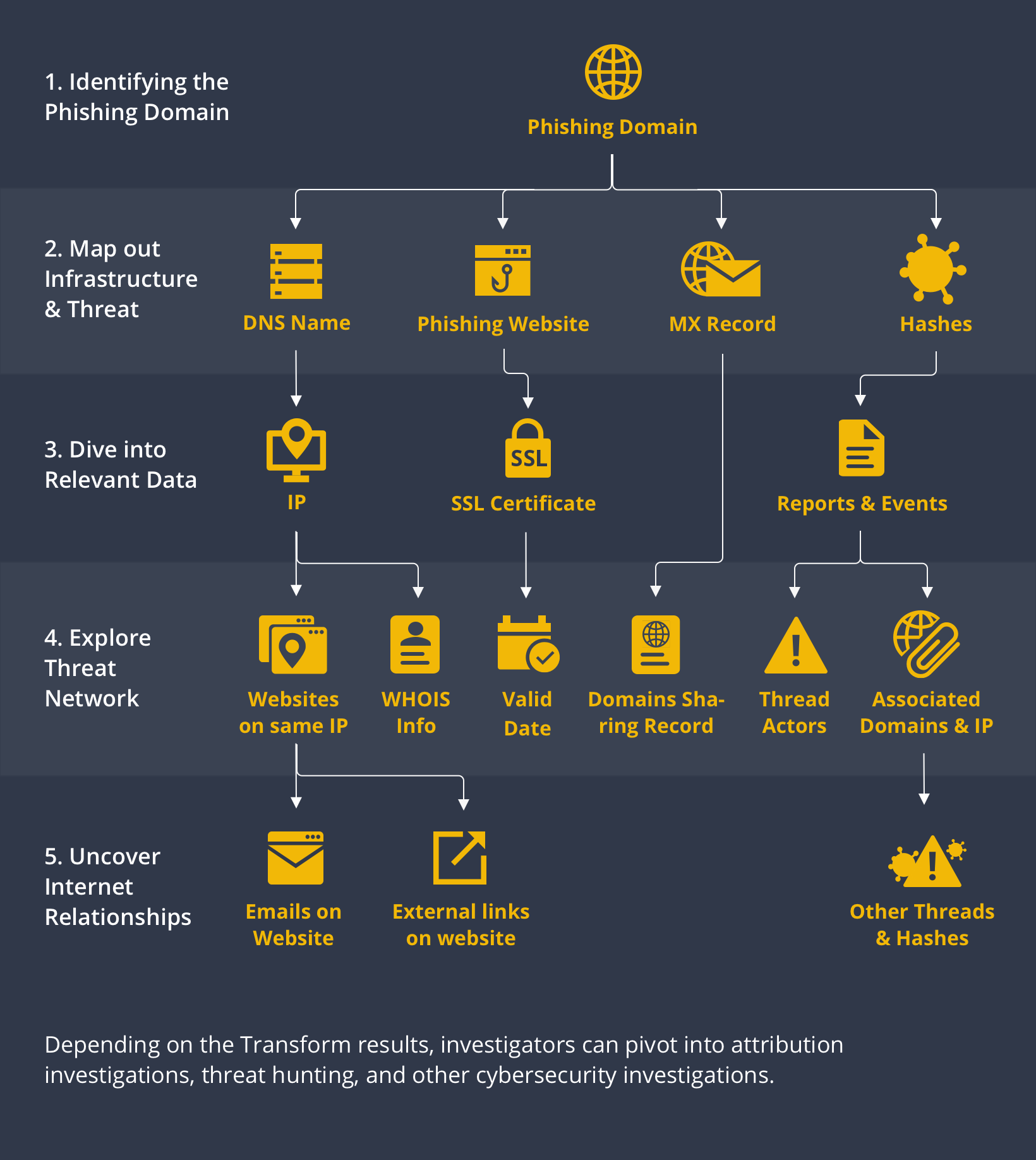
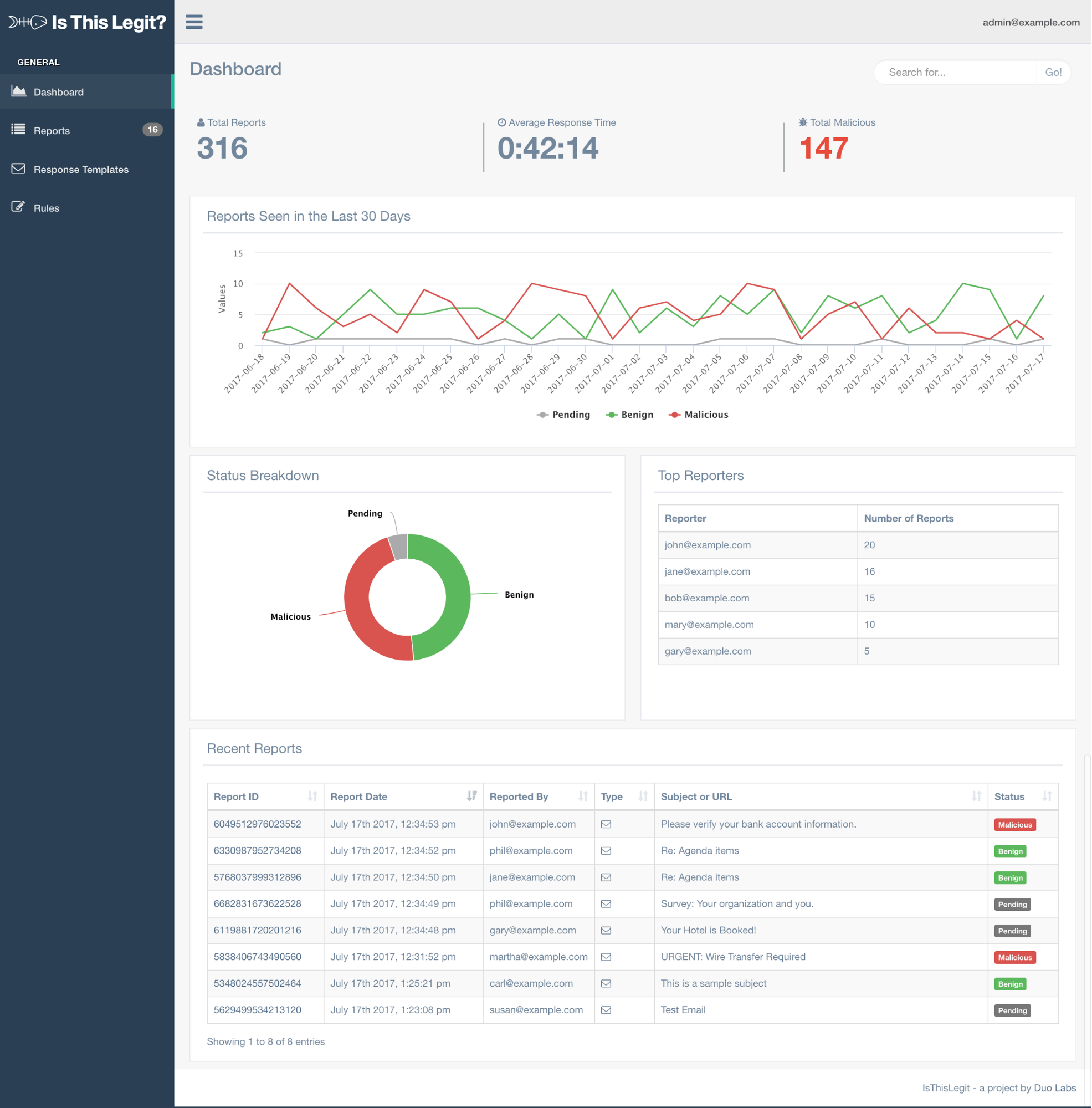
Ptrace Security GmbH on X: "ThePhish: an automated phishing email analysis tool https://t.co/XjKijRydiw #Pentesting #WebSecurity #Phishing #Infosec https://t.co/RmhGCPBriU" / X