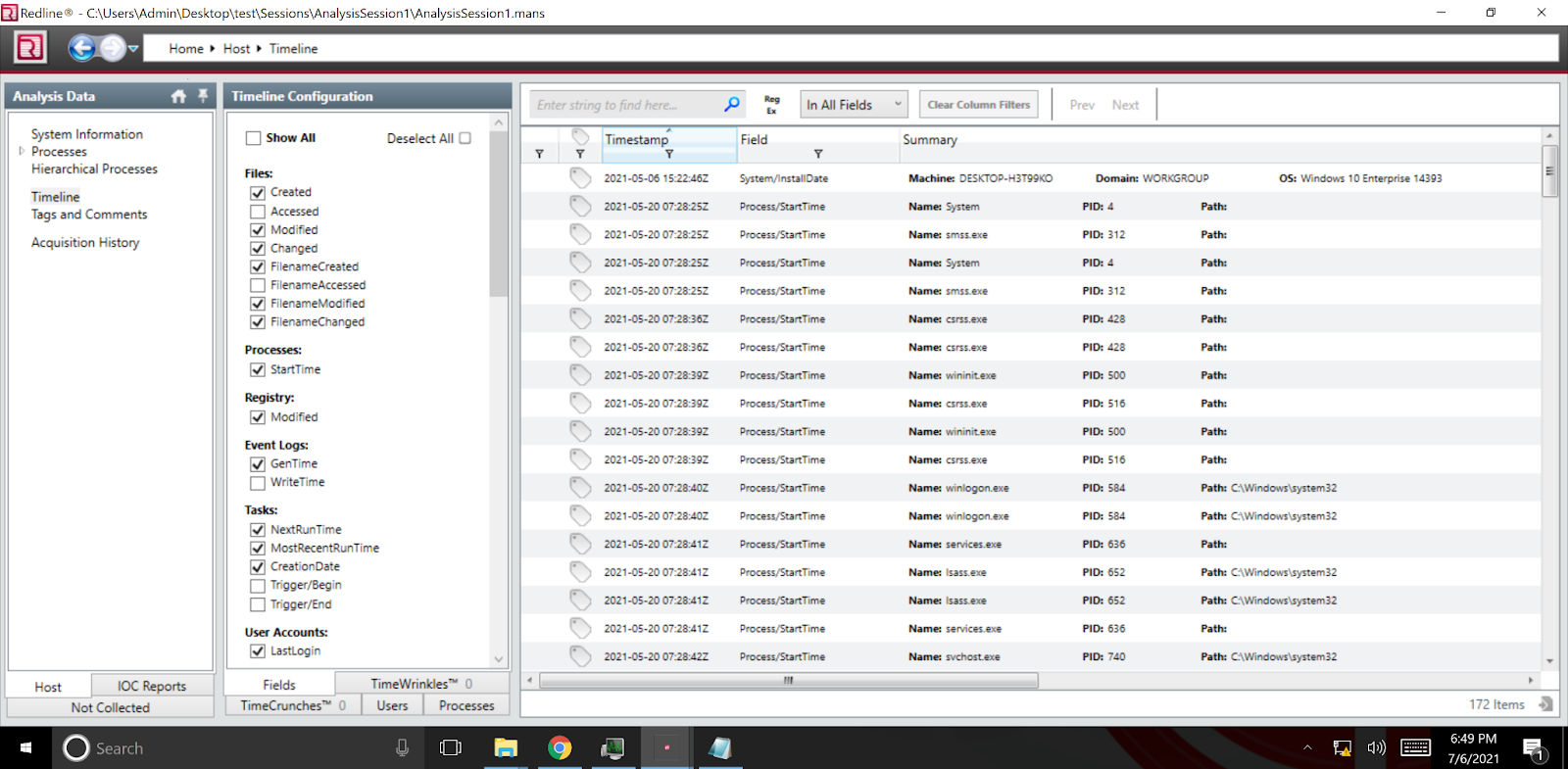
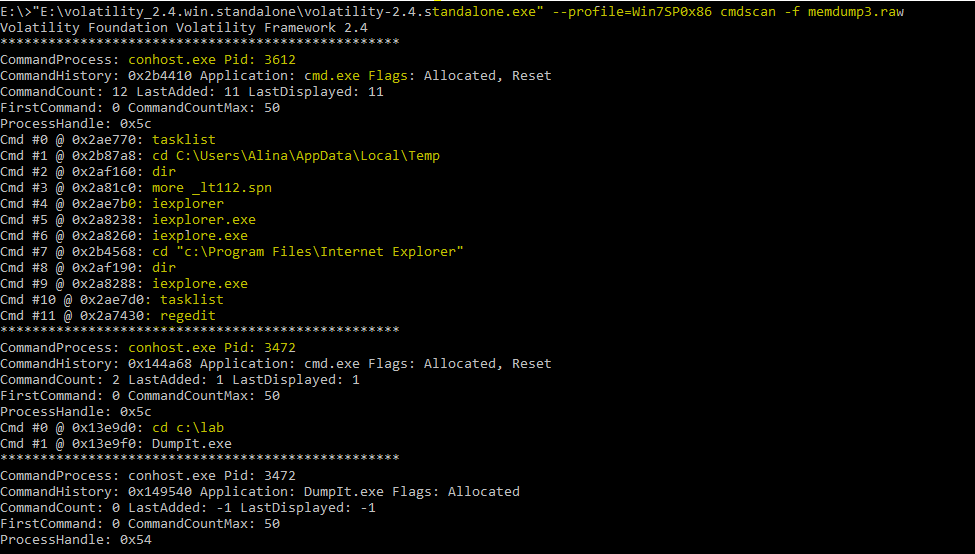
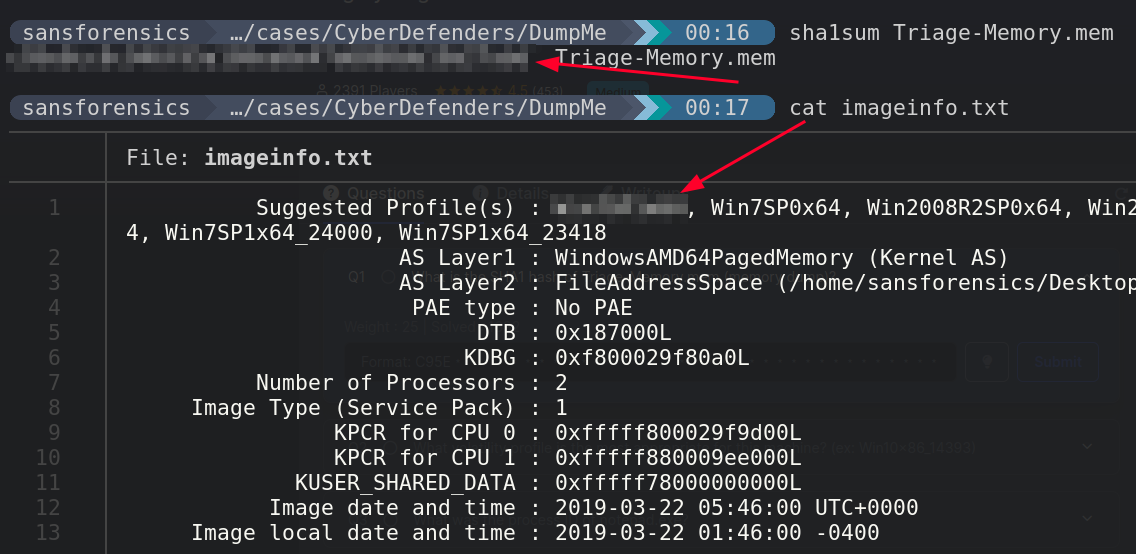
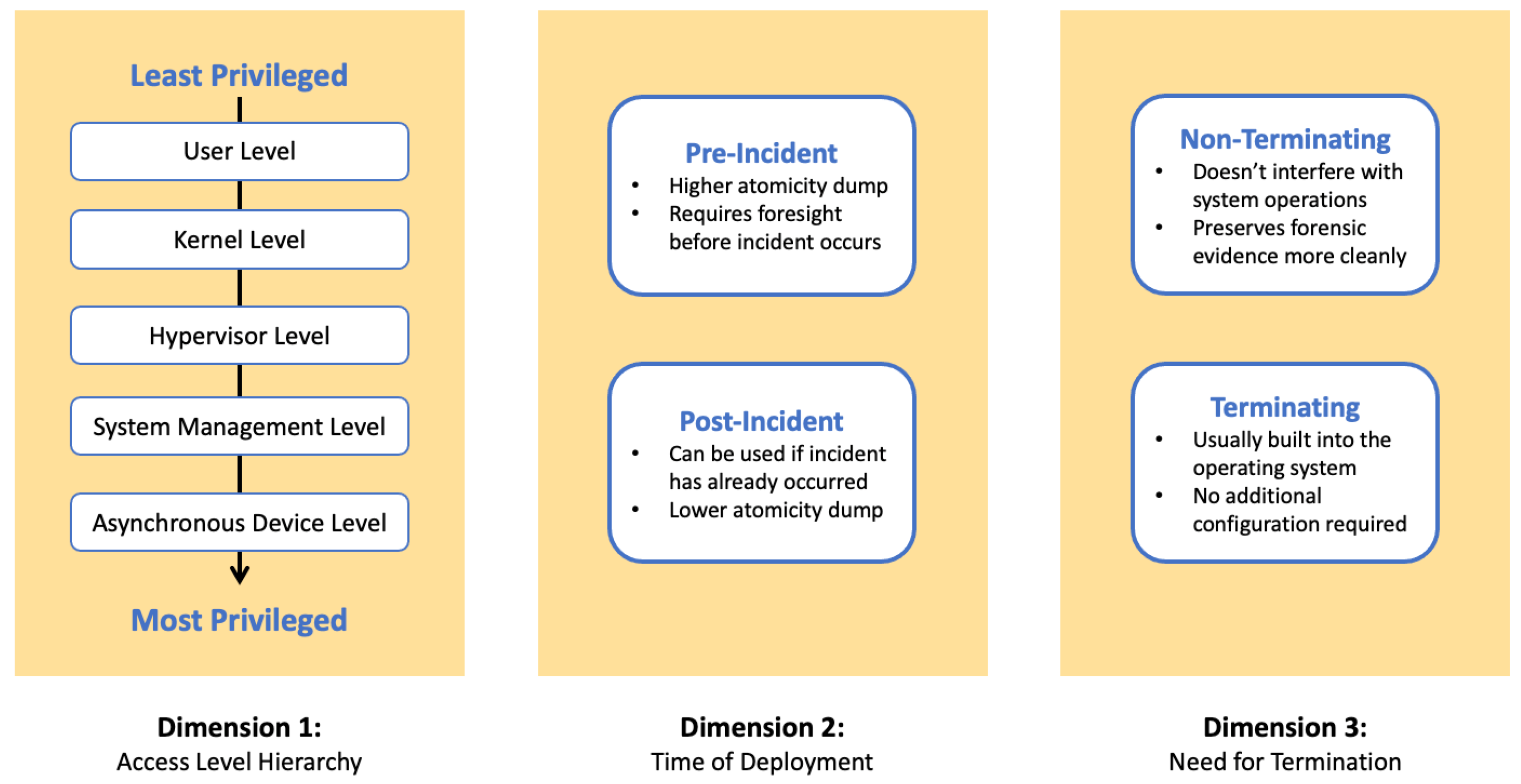
Memory forensics tools: Comparing processing time and left artifacts on volatile memory | Semantic Scholar

The Art of Memory Forensics: Detecting Malware and Threats in Windows, Linux, and Mac Memory. : Hale Ligh, Michael, Case, Andrew, Levy, Jamie, Walters, AAron: Amazon.fr: Livres

Signature based volatile memory forensics: a detection based approach for analyzing sophisticated cyber attacks | SpringerLink