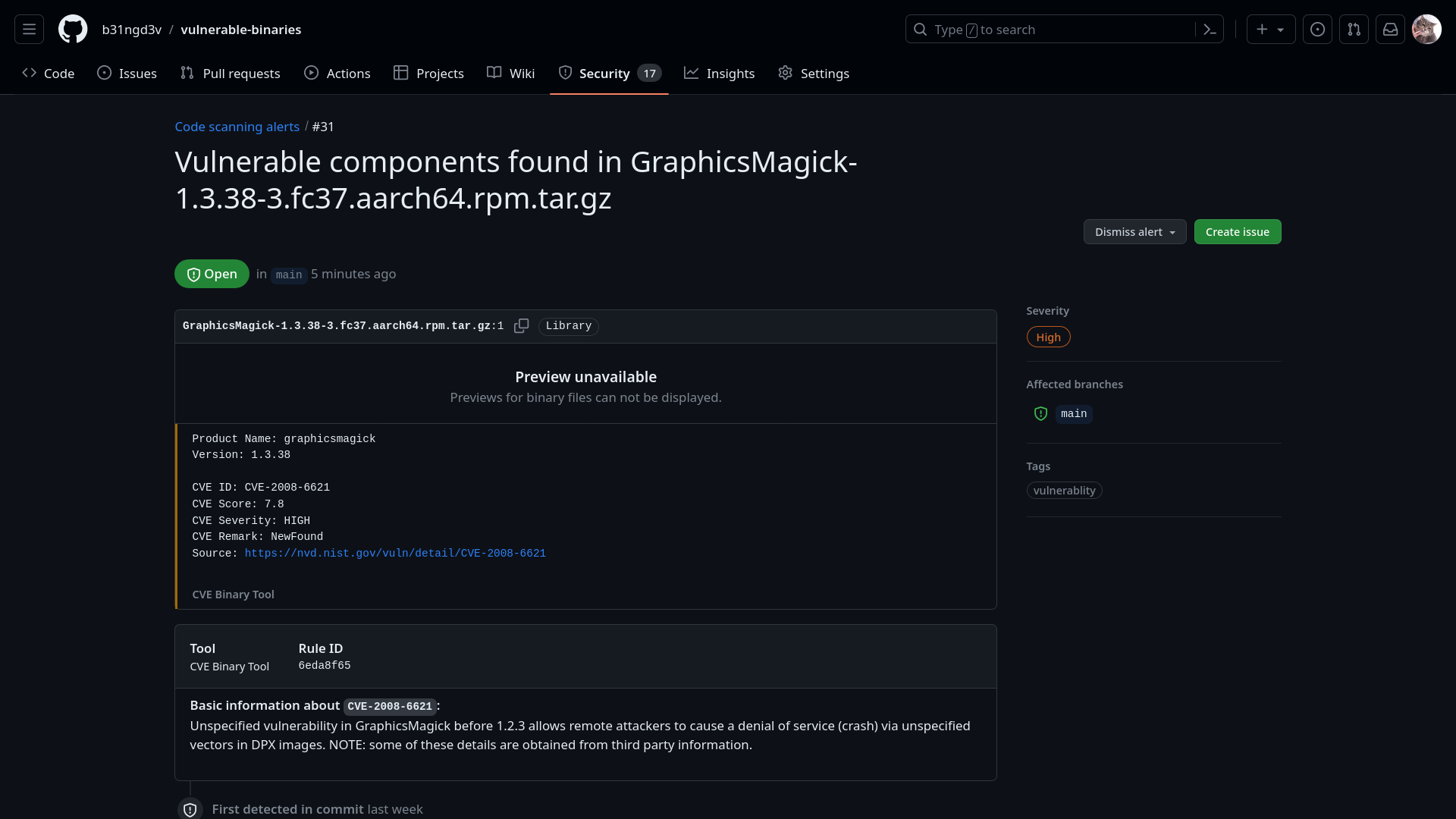
Microsoft Security Code Analysis – a tool that seamlessly empowers customers to enable security controls in your CI/CD pipeline - Developer Support
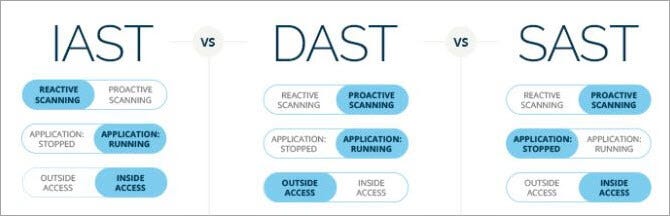
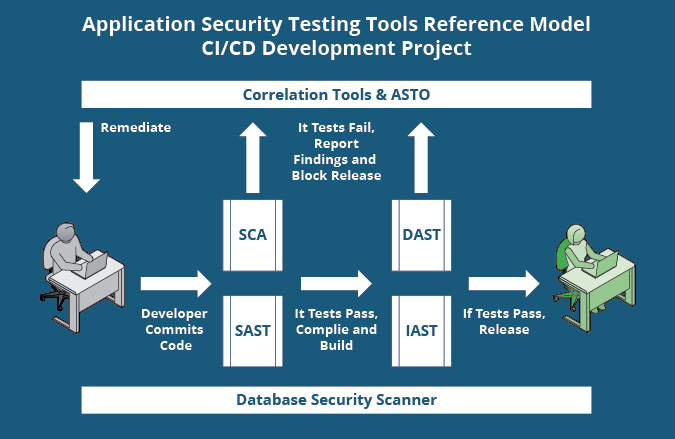
Ensuring Robust Application Security: Exploring SAST, DAST, and IAST for Comprehensive Protection | by Ranjan Singh | Medium
How does static binary analysis work? What type of internal modeling is performed (e.g., dataflow, controlflow, etc.)